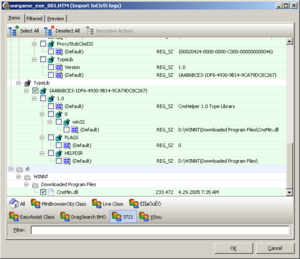
Importing an InCtrl5 log
InCtrl5 is a popular tool that monitors changes to the registry and file system and logs them to for example HTML files. OpenSBI Edit Lite is able to import such logs to give you a quick start into writing new SBI files.
Quick Steps
- Run OpenSBI Edit Lite.
- Start a new file (menu File: New).
- Open the import dialog (menu File: Import: Import InCtrl5 logs).
- Select one or more HTML log files as created by InCtrl5.
- Make your choice of changes to detect by selecting the checkboxes next to them.
- Finish by pressing the OK button.
- Add useful descriptions for files (see description templates).
- Update the advanced file parameters where required (see the tutorial Choosing advanced file parameters).
Details
The import dialog will give you three tabs:
- The tab Items shows the contents in a structured view:
- The root level of the structure will be root registry keys and drives that changes appeared on.
- Levels in the structure that were not changed and are displayed for better viewing are displayed with grey icons and no checkboxes.
- Where registry items and files are detected to be associated with one another, they share the same background color. As an example, this will combine a BHO, the associated CLSID, typelib, interface and file.
- The toolbar at the bottom will show buttons that will filter the list to display only those items that belong to the selected group.
- You can type in any term into the filter field to display only those items that include the filter term. Remove any text in the field to undo the filter.
- The one named Filtered will show you any items you've suppressed on the main view. If you right click any item here, you'll be able to make it visible in the Items list again. Reasons for permanently suppressing items would for example be registry changes to various MRU lists that are not related to malware.
- The last tab, Preview, shows you how the OpenSBI code for the selected entries would look like. This is the same code that will be added to the file you've opened in the editor.
Warning
Not all changes that happen while a malware is installed are associated with that malware. Windows itself does update MRU (Most Recently Used) lists in the registry, for example. Malware might also install legit third party libraries for it's purposes. The InCtrl5 import allows rapid detection prototyping, but you still need to pay a lot of attention to avoid false positives.
InCtrl5 is also not a complete monitoring tool; it will probably not list a lot of rootkit activity, WMI changes are difficult to recognize if at all, and the same goes for various other API calls that update binary files, where you will notice only that the file has changed, not what exactly was changed.